How To Maintain Security When Employees Work Remotely
How To Maintain Security When Employees Work Remotely

Working from home can be a lucrative career option for one. Working remotely offers the benefit of location flexibility. Telecommuting is growing in popularity, and data security has become a greater concern for protecting remote employees.
Work from home provides a good work-life balance to the employee, increases efficiency, and helps the company accomplish its goal. Providing a remote working option for the organization itself reduces organization expenses in the number of overheads.
However, organizations also face security issues when their employees work from home. Due to the COVID-19 pandemic, many companies offer “work from home” options. As per the stats,
- Over 67% of employers surveyed allowed employees to work from home who do not normally do so.
- 36% actively encouraged all the employees to work from home in some or all parts of the country.

To ensure data security, protect sensitive information, or secure remote workers, organizations must provide employees with the systems and software they need.
Even though it can increase organizations’ costs, it is a one-time cost, and these costs
are taken as the purchase of assets in organizations.
According to The State of remote work 2021
- 74% of Americans need a continued remote working arrangement to stay at their current job.
- 85% of Americans prefer to apply for jobs that offer remote flexibility, while just 15% would apply for a position that requires total full-time office work.
Learn more: Performance Management for Remote Employees: 21 Best Practices 📝👨💼
Benefits of Remote Working
Working from home offers many benefits for both parties: company and employee. Some of the advantages that employees and companies can enjoy through work from the home concept are listed below:
- Flexible schedule
- Increase productivity
- Work without distractions
- Comfortability and less stress
- A great number of applicant
- Profitable in terms of resources
Security Risk factors Associated With Remote Working
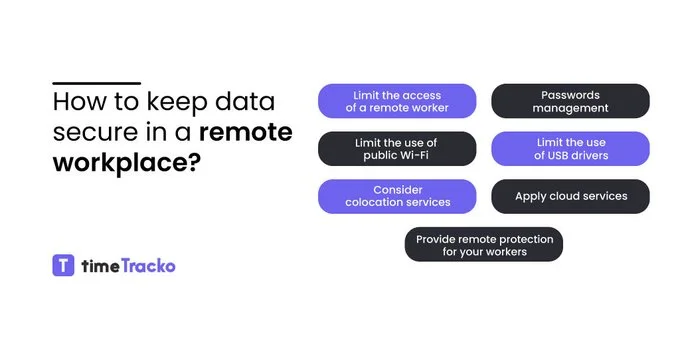
The practice of remote work has become popular and commonplace worldwide in recent years, and cyber-security has become a major concern for companies trying to secure remote workers.
Employees working remotely may be unknowingly endangering your company’s data. There is a risk of data breaches, identity fraud, and other negative consequences when working from home.
Some factors associated with security concerns when working remotely include the following:
1. Using Weak Passwords

In spite of the fact that organizations use VPNs, firewalls, and other cyber-security systems to safeguard their remote networks, human error still occurs when employees use weak passwords to protect their accounts.
It is easier to exploit human error than to crack sophisticated security software, which is why hackers attempt to crack account passwords to gain access to company information.
Password repetition is another common insecure practice used by cybercriminals. The moment they crack the password to one account, they will try to gain access to other accounts using the same password.
Employees whose passwords are repeated across both their work and personal accounts are at greater risk of becoming victims of a cyberattack.
2. Working From a Personal Device
The convenience of working from personal devices may make employees feel more free and flexible, but these devices pose a security threat.
Employees who use their personal devices for work-related purposes should be fully aware of the risks involved. Frequently, employees leave companies and leave behind confidential data, which will not be wiped when they leave the company.
For example, they might suddenly leave the company and leave behind the confidential information they have stored on their device during their employment without allowing you to erase it.
Organizations typically provide employees with work computers, but some let remote employees use personal computers to help improve workplace culture.
However, while policies are usually meant to make processes more flexible, they can also leave company data vulnerable since personal computers are not nearly as secure as work computers.
3. The Practice of Encrypted File Sharing

The major challenge most organizations face with their data security is that
although they are wary of encrypting data while stored on their network, they are far less likely to secure it once it’s in transit.
Every day, your employees share private data about your clients and your company, ranging from client account information to files, so you can’t afford to let a cybercriminal access this information.
It is possible that sensitive company information could be intercepted, leading to identity fraud, ransomware cyberattacks, theft, and others.
4. Insecure Wifi Networks

It is possible that your employees are accessing their corporate accounts via unsecured public Wi-Fi at home or on their own wireless network. As a result, malicious actors nearby may be able to easily monitor their connection and steal confidential information.
Cybercriminals could intercept and steal data sent in plain text in an unencrypted form. Due to this, you should not allow your employees to access any insecure WiFi networks unless they are also connected to your VPN for Remote Work.
5. Phishing Schemes

A remote employee can become the biggest security risk for your network. It is possible that your employees are providing threat actors with access to your network and the private information of your company by following cybersecurity worst practices without knowing it.
Phishing schemes are one of the top cyber threats for remote employees.
Phishing schemes are meant to trick a victim into providing sensitive information or credentials that can be used to hack accounts, steal more personal information, or commit identity fraud.
It is becoming increasingly difficult for employees to detect phishing emails as they become more sophisticated, especially when phishing emails make past email filters straight to employees’ primary inboxes.
Learn more: 7 Challenges With Solutions for Managing Remote Employees👨💼👨💼
Tips & Tricks for Keeping Employee Data Secure When Working Remotely
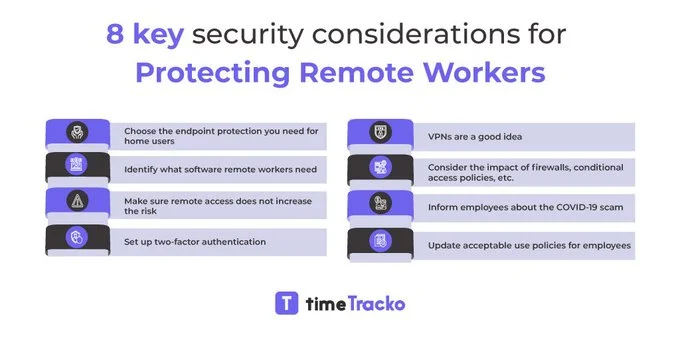
You must secure remote workers by taking the following measures:
Create a Policy
Every organization has some rules and policies that employees need to follow to maintain discipline. It would help if you created policies to run day-to-day operations smoothly.
Policies are the road map and guideline for smooth internal and external business operations. However, policies will not benefit organizations if you only make the policies and are unwilling to implement them.
Companies should make policies that it is beneficial for both employees and employers. You should ensure that policies are flexible enough.
When a company has a remote team, team members are distributed in different parts of the world. Therefore, Companies can secure remote workers by implementing policies for remote teams.
Some standard policies that an organization should set are working hours, cybersecurity, equipment used, communication, and more.
For example: When you provide employees with a laptop, then you set some policies and rules like not sharing a computer with others, using it only for office work, and more.
The essential security clause that should be included in your remote work policy is:
- It is important to define which job titles are eligible for remote work.
- Provide them with tools and platforms to use.
- Set up a system for employees to follow if their accounts are compromised.
Learn more: Managing remote employees: tips that you should follow 🙌 🙌
Ensure Employees’ Internet Connections are Secured
The main concern of employers is their data security when their employees are working remotely. Employees should follow the organization’s data security policies, ensuring that their data is not exposed to third parties.
Sometimes, employees might use the public network and work from cafes, coffee shops, or libraries. While using public networks, employees should connect with Virtual Private Network (VPN).
You should provide your remote team with VPN so that they can connect to any network without any fear.
VPN ensures secure communication and sharing of files without fear of getting exposed. It secures passwords and sensitive data and protects such data from third parties.
It would be best if you determined the following criteria:
- Security
- Speed
- Strong Encryption
- Censorship
- Streaming
- Number of Servers
- Unique IP addresses and more.
Learn more: How to Monitor your Employees’ Internet Usage🌐🌐
Use Two Factor Authentication
Remote employees can use two-factor authentication to secure their files and data from third parties’ access.
A growing number of organizations are adopting two-factor authentication (2FA) for data security management. A user confirms their identity by initially providing a username and password, followed by another piece of information, such as an answer to a “secret question” or a PIN sent to their cell phone.
When working from home, sometimes your family members or roommates might use your PCs. To ensure no one can access your data, you can use two-factor authentication in your files and data.
Usually, employees add passwords to their files and folders; however, passwords can be easily hacked. Therefore, you should add a PIN code while adding a password that ensures a high-security level.
Whenever anyone tries to access your files and folder, you will receive a PIN code on your cell phone, and you can get notified about such actions. You can also add multi-factor authentication like fingerprint, retina, voice recognition, etc.
This factor helps to minimize the chances of fraud and minimizes trust issues. It also increases work productivity as employees can share their files and folders without fear of being misused.
Learn more: Best Data Security Practices for Remote Workers in 2022🔓🔓
Use Firewall and Antivirus Software
Another important measure to follow to protect remote workers is a firewall and antivirus software. The organization should provide employees with Firewall and Anti-virus to provide security from malware and cyber threat.
Using a firewall will further strengthen the security of your employees’ devices by preventing unauthorized access to and from the network. The purpose of firewalls is to monitor network traffic and block unwelcome Internet traffic.
As a result, firewalls are essential tools that will protect your remote endpoints from various cyber threats that may be encountered. Besides firewalls, organizations should provide their employees with good anti-virus software that protects employees’ PCs from viruses, malware, worms, Bots, and more.
Learn more: Best Productivity Apps for Employees Working From Home✅✅
Keep Updating Programs and System
Remote working is all about telecommuting, and employees need to depend on programs and systems to complete all their work.
Sometimes software and programs can have bugs, and hackers can identify them and hack your system. They can steal all data and information stored on employees’ PCs.
Program and software updates bring additional security features, fixed bugs, and regular updates, which are essential for system security. Software updates minimize security problems that customers are facing while using the software.
However, employees procrastinate to update their computer programs and system, due
to which sometimes their system can face some threats. It is important to ensure that employees know how to run software updates regardless of whether they use company equipment or their own.
Patches or software updates add new features, enhance stability, add security features, and eliminate obsolete features. Make all your remote devices update automatically to keep up with the latest patches.
Learn more: Best Practices for Managing Multiple Projects Efficiently📝📝
Use Communication Tools
Communication among the remote team can be challenging if the right communication tools are not used. And using social media to communicate about any subject matter related to work might not be effective.
When employees work from the office, they can instantly communicate whenever they are stuck on some problem. But when employees are working remotely, they may not communicate as they communicate in person.
Therefore, you should ensure that employees are using proper communication tools for office communication. You can use messaging apps like Microsoft Teams or Slack.
You should select those apps that provide all-in-one features like video and audio conferencing, chat systems, file sharing, etc. These apps can create a group according to projects, team members, departments, etc.
You can also share
- office notices,
- new rules,
- upcoming events in such messaging apps,
- can have one-to-one communication or group communication using messaging apps
- can view each other online status, making it easier to view employees’ availability and message them.
Learn more: Best Employee Communication Tools For Organizations😜😜
Provide Proper Time Tracking Apps
Remote teams and onsite workers can find time tracking challenging. The frequent checking of employees could lead to a lack of trust between employers and employees.
Time Tracking apps allow you to see employees’ computer activities in real-time and enhance employees’ performance. It also ensures that employees are paid based on their work performance.
When employees know their work is being tracked, they automatically try to give their 100% effort in their job. It helps increase employees’ work productivity, and they can achieve more in less time.
With these apps, you can also manage employees’ schedules and send employees notifications about their work schedules. It provides employees the flexibility to manage their shifts according to feasibility.
Learn More: Workplace Productivity Tips: 15 Secrets to Success🚀🏆
Provide Project Management Tools
Project management tools are essential for both onsite and remote employees as they can manage their projects effortlessly. It ensures that all your project plans are achieved within the specified time and that you do not miss any plans.
You can create projects, divide the project into different tasks, and assign tasks to employees using the apps. It allows you to set deadlines and budget limits for your projects.
It ensures the privacy of your projects, files, and data that you share using these apps. Also, it stores the shared files and folders and provides you with them whenever you want. These apps also ensure project profitability by managing the resources needed for business and tracking project profitability. There are many project management apps that you can select for your business. Popular project management apps are ProofHub, Trello, Asana, and more.
Learn more: Work Remotely with the Best Remote Work Tools 💻 💻
Create Lock for Your Devices
Employees should keep a lock on their devices so that no one can use their devices without their permission.
Employees can keep passwords on their PCs, and routers, and lock their screens to protect their system from unauthorized access.
Locking your devices protects your files, folders, financial statements, client information, etc. Some devices allow you to automatically lock the screen, while others will manually set the lock.
Create Employee Cyber Security Training
The first step to securing remote computers should be to encourage employees to lock their computers when traveling physically. If the device is not physically accessible, there is little chance of foul play taking place.
Secondly, employees need to be aware of potential observers when entering sensitive information, such as logins and passwords, in a public area. our livelihood can be protected by affordable solutions no matter how big your business is.
Lastly, help them learn about identity theft protection. There are several ID theft protection services available out there, and it will be good for remote workers to do proper research to know which ones came out on top based on the testing of these services.
Establish a Security Response Plan
You must ensure that your technical support team responds swiftly in instances where a remote employee is threatened with ransomware or data breaches. Ensure that remote workers have direct access to technical support and reporting issues (dedicated e-mail, phone line, etc.) so they can seek assistance as needed.
In the event that data is lost, it is highly recommended that you build a clear action plan in order to prevent further damage, restore functionality, and recover critical data. Do not leave any doubt as to what action you will take.
Final Words
Remote workers should always use VPN (Virtual private networks) when working outside the office. Employees should be encouraged to lock their computers when traveling physically as the first step toward securing remote computers.
Secondly, employees should ensure that any observers are aware of their presence when typing sensitive information such as log-ins and passwords in a public area.
However, while providing remote working options, the organization should follow the measures mentioned above to protect remote employees and data from third parties.
FAQs About Remote Security
What is remote access security?
The term “secure remote access” means protecting your network, its resources, and any confidential or sensitive data by implementing a security policy, solution, or strategy.
What is the most important security precaution you should take when working remotely?
When it comes to securing trans-network communication, Virtual Private Networking (VPN) is often considered to be the best solution. Employees should be provided with work-from-home security tips and guidance regarding being a secured remote worker. Companies need to beef up their VPN security.
What is the most common security remote work security risk?
-> Weak remote access policies
-> Lack of visibility into remote user activity
-> Weak passwords
-> Phishing emails
-> Unencrypted file sharing

 in Melbourne
in Melbourne 
 Employee Screen Monitoring Software
Employee Screen Monitoring Software App and Website Monitoring Software
App and Website Monitoring Software Time and Attendance Software
Time and Attendance Software Finance
Finance Banking
Banking Healthcare
Healthcare Lawyers
Lawyers Retail & ecommerce
Retail & ecommerce Knowledge base
Knowledge base Blogs
Blogs Installation Guide
Installation Guide FAQs
FAQs About
About Media Kit
Media Kit Contact us
Contact us